Leveraging MITRE ATT&CK Framework for organizing your threat reports
Antoine Cailliau
Author
As cyber threats increase in sophistication and volume, it becomes more important for organizations to have a framework for analyzing and responding to these threats. The MITRE ATT&CK framework is one such framework that provides a structure for organizing threat data and improving threat analysis. In this blog post, we will discuss the usefulness of the MITRE ATT&CK framework for organizing your threat reporting, how to use the framework to organize reports, and how to effectively use MITRE ATT&CK in your organization.
MITRE ATT&CK framework provides a common language
The MITRE ATT&CK framework is a powerful tool for threat analysis. It provides a common language for reporting and knowledge sharing, and it helps to standardize the analysis process. The framework is divided into 14 techniques, each representing a different stage of an attack. This makes it easy to track an attacker’s progress and identify gaps in your collection of reports. Additionally, the ATT&CK framework is constantly updated with new information, making it an invaluable resource for security professionals. Thanks to its usefulness, the MITRE ATT&CK framework has become the industry-standard tool for threat analysis.
Using a framework helps you find quickly the right threat reports
Being able to easily and quickly find the information you need is essential when it comes to security threat reports. That’s where using a framework can be helpful. By creating a structure for your reports, you can ensure that information is organized in a way that makes sense and is easy to find. Plus, using a framework can also make it easier to spot trends and track statistics over time. When it comes to choosing a framework, there are a variety of options available. The key is to select one that will work well for your organization and meet your specific needs. For many professionals, MITRE ATT&CK is a good solution for labeling and organizing your security threat reports.
How to effectively use MITRE ATT&CK in your organization?
Here are some tips on how to effectively use it in your organization.
-
Tag each threat report with the relevant ATT&CK technique or sub-technique. This will help you keep track of popular techniques leveraged by threat actors.
-
Standardize your labels. This means making sure that all the information is consistent and in the same format. This will make it easier to search and mine for insights.
-
When searching for specific and relevant information, make sure you filter on the techniques that are relevant to the threat.
-
Finally, take advantage of visualization capabilities. When your data is properly labeled, you can look at the data in many ways: including graphs, heatmaps, and matrix views. Experiment with different views to see what works best for your organization.
How DocIntel can leverage the MITRE ATT&CK framework?
DocIntel can help cyber threat analysts to consistently and efficiently organize threat reports based on the MITRE ATT&CK framework. By automatically tagging and categorizing reports, DocIntel can save analysts valuable time that can be spent on more important tasks such as analyzing the data and providing insights.
By automatically importing all of the existing techniques as facets and tagging them in DocIntel, you can ensure that all future threat reports are properly mapped to the right ATT&CK technique. Users can then leverage DocIntel’s powerful search and filtering capabilities to quickly find the reports they need.
DocIntel automatically extracts the techniques from any new document you upload, so all that’s left for you to do is double-check the labels. This makes the entire process much more efficient.
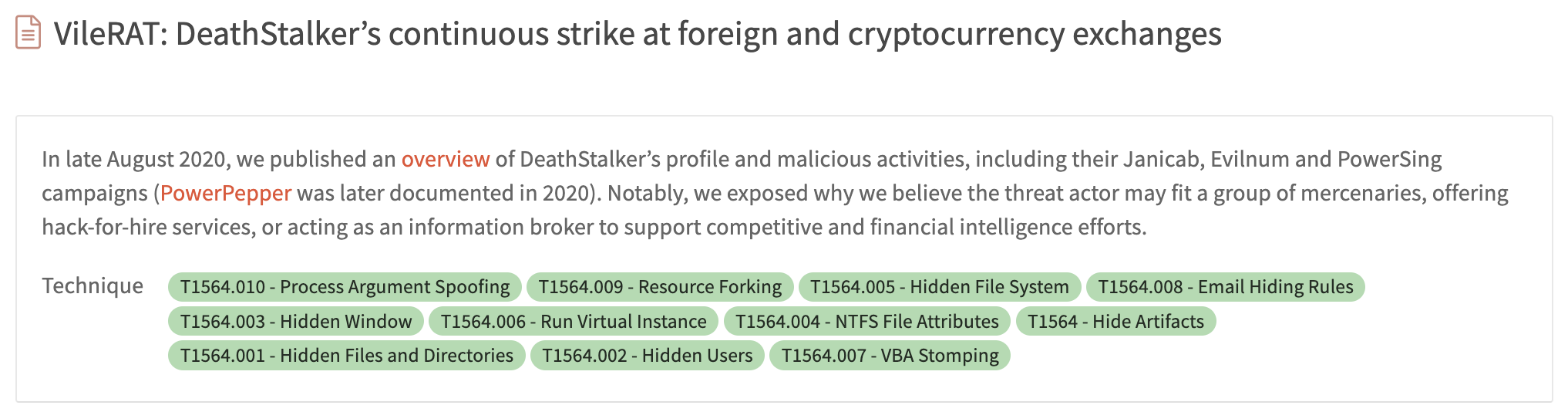
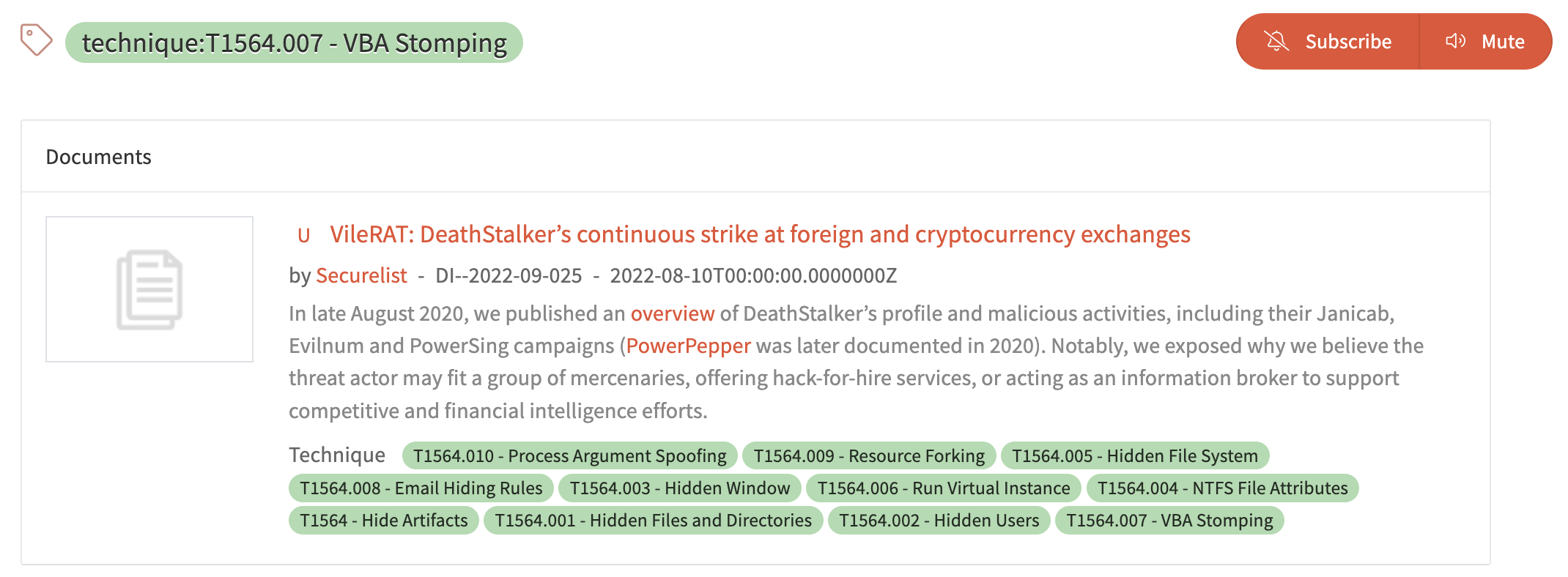
The beauty of categorizing techniques as tags is that you can pick and choose which ones are most relevant to you and receive notifications whenever something new gets published.
Conclusion
The MITRE ATT&CK framework is a powerful tool that can be used to organize your threat reports. It helps to organize information and provides a common language for analysts to use when classifying and labeling threats. Tagging your documents in DocIntel with MITRE ATT&CK tags will help you to more effectively organize and leverage your threat reports in your organization.