Use Cases supporting
threat intelligence
DocIntel is tailored to the CTI analysts. It supports them in their activities, from daily watch, to support to security operations and incident response and, their core business intelligence analysis.
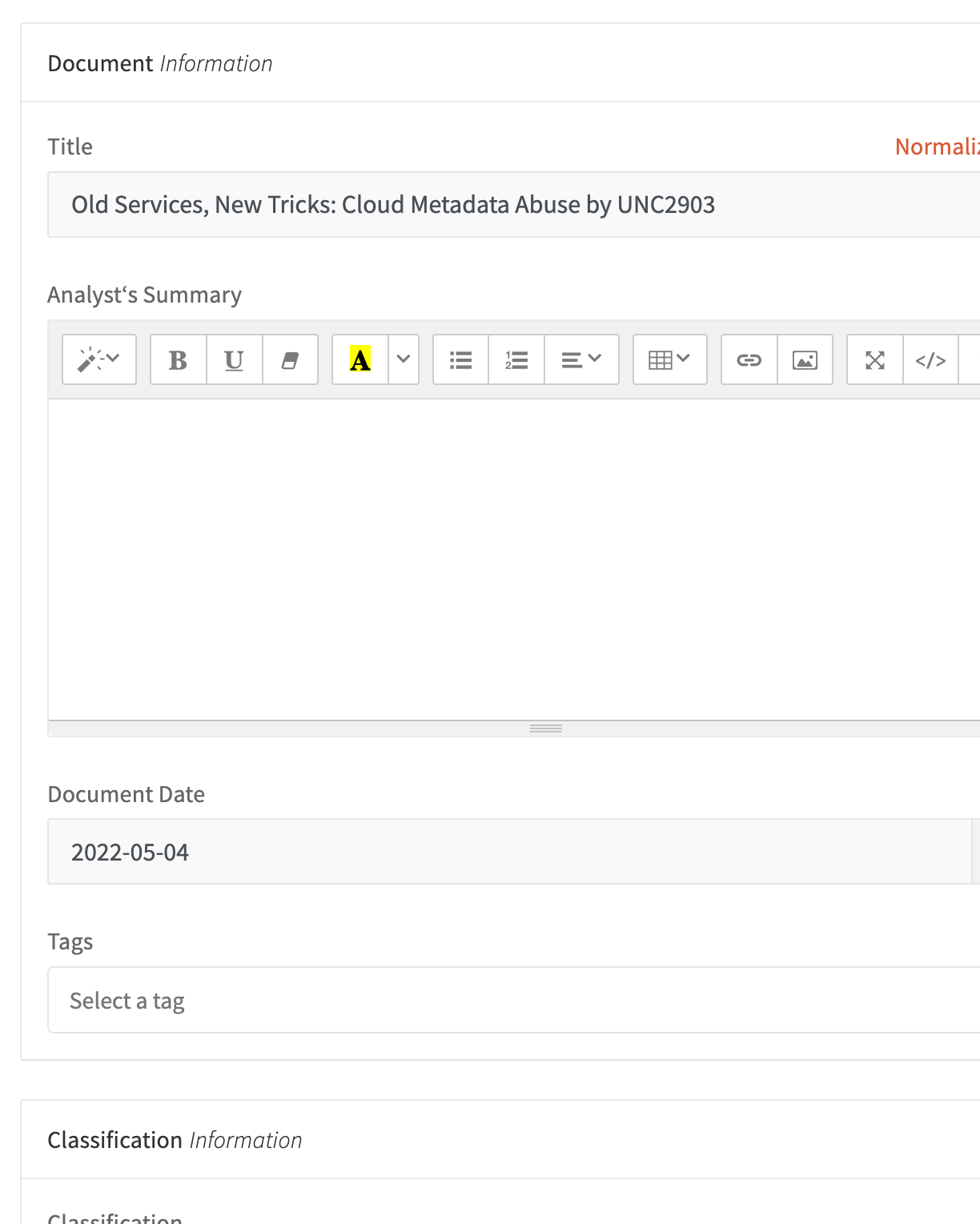
Daily Collection and Processing
The analyst collects and process the daily blog posts, open-source and private reports received.
Automate
DocIntel collects from mailboxes, commercial
and RSS feeds.
Pre-Process
DocIntel extract vulnerabilities, TLP, actor names, as well as observables (e.g. IP addresses)
Review
The analyst review the pre-processed documents and adds the relevant tags.
Enjoy
The processed documents are available to everyone, and will be included in newsletters.
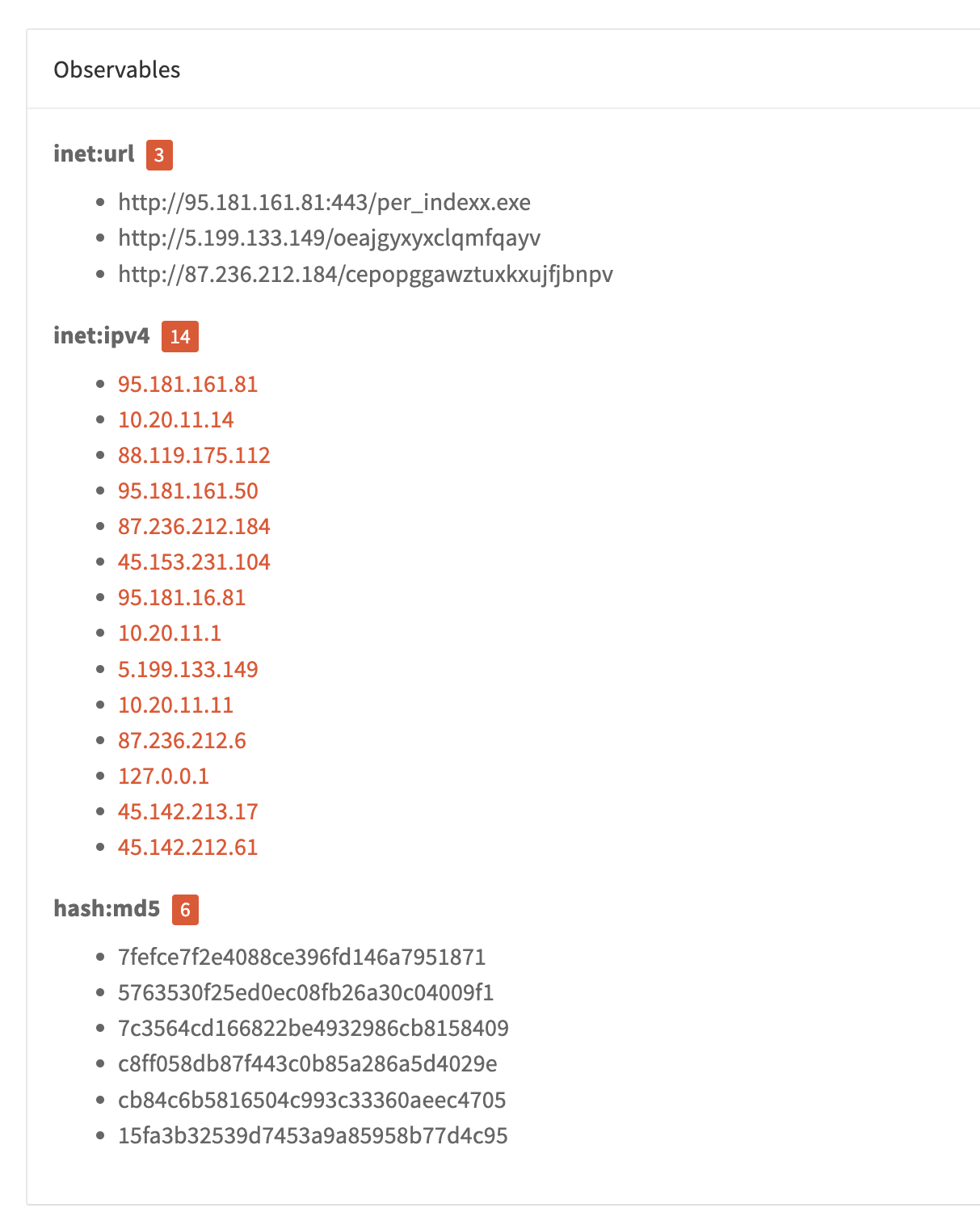
Assess relevance of an observable alert
The analyst collects and process the daily blog posts, open-source and private reports received.
Efficient search and filtering
DocIntel support full-text searches but also obfuscated observables such as 1[.]2[.]3[.]4 or example[.]org.
Complete context
DocIntel provide the analyst the extracted observables but also the original source of the information. Don't miss any detail.
Complete API support (and Python client)
Plug the knowledge base into your existing tools to enrich or contextualize the information to help analysts.
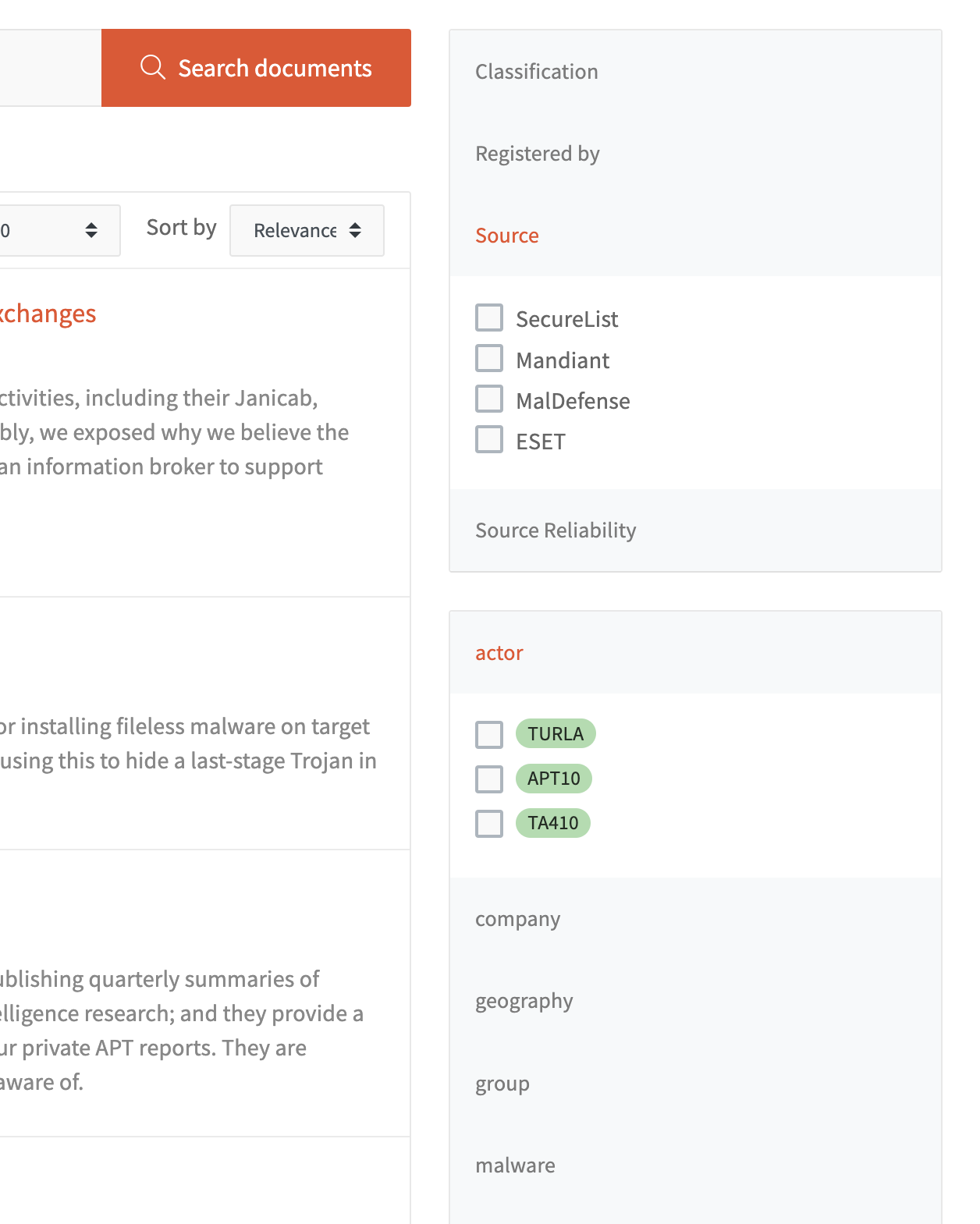
Quarterly Analysis for Strategic Intelligence
Quarterly reports comprehensively summarize the relevant intelligence over a 3-month period. The Strategic CTI analyst extracts and reviews the ingested reports and news collected during a quarter to produce such strategic intelligence report.
DocIntel provides advanced filtering and search options so that the analyst can extract only the relevant reports.
- Filter on publication or registration dates
- Filter on tags (e.g. specific actors or regions)
- Filter on source or source reliability
- Filter on classifications
- Filter on users
- ...
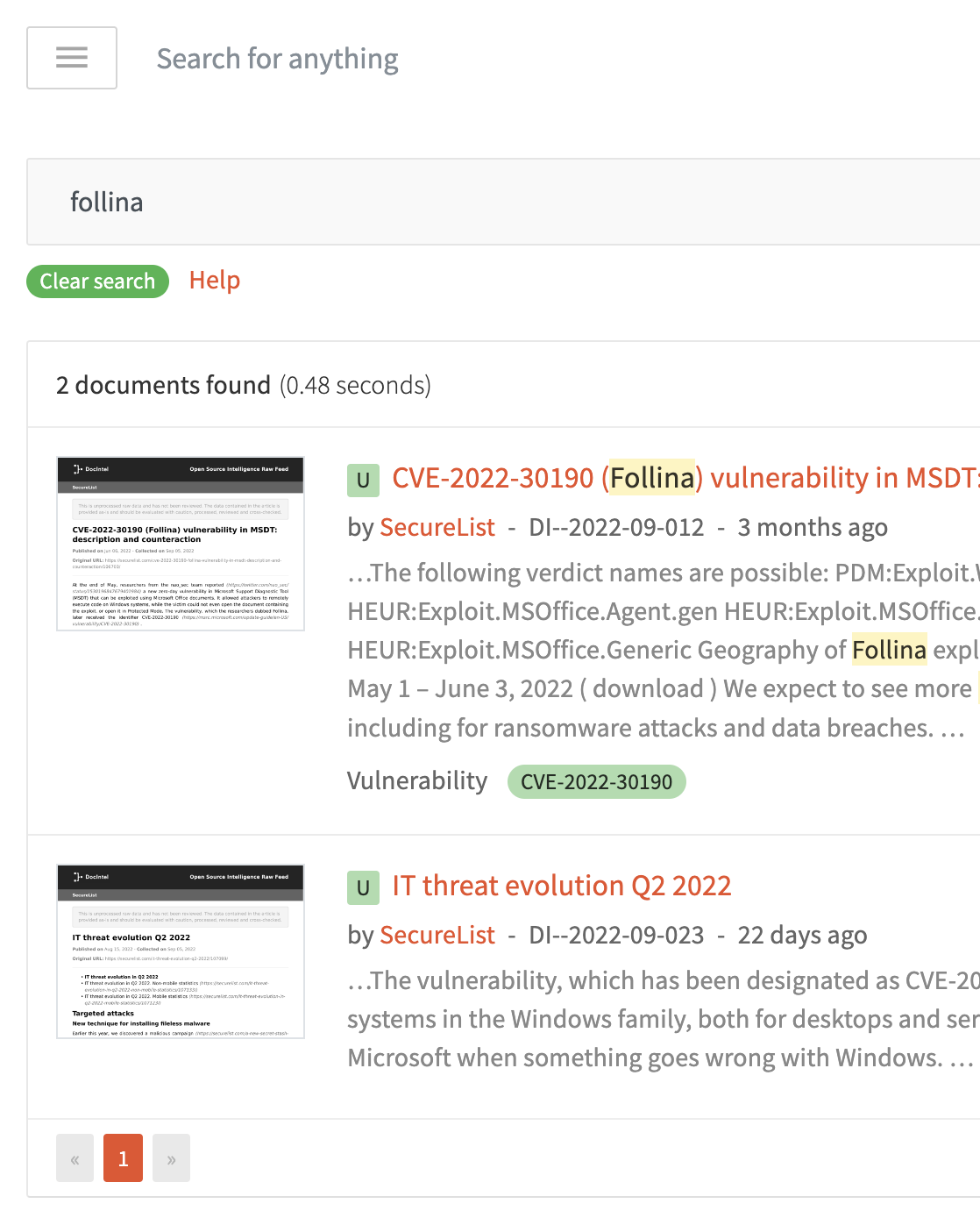
CTI Support for Incident Response and Forensics
In the heat of an incident, rapid access to relevant information is often key.
Find what you know!
Identifying vulnerability reports helps the first responder to pinpoint additional detection or mitigation.
Identify what you don't know!
Finding threat reports documenting an attack by an APT helps CTI analysts to formulate investigative questions to identify malicious activity that might have occurred before or after the exploitation.